The spread of COVID-19 has disrupted the world’s health, economic, political, and social systems.
Simultaneously, a threat growing in the digital space has been developing and refers to the risk of cyber-attacks with hackers taking advantage of the increased dependence on digital tools and the uncertainty of the crisis. Cybercriminals use social engineering with topics related to COVID-19 due to heightened visibility.
There have been multiple cases of cyber-espionage carried out by organized groups and many times sponsored by governments. One such group of Chinese and Iranian origin, backed by their respective governments, allegedly are exercising cyber-espionage using a COVID-19 theme as an attack vector.
In many cases, the espionage carried out by these groups is directed at other countries and sometimes to the citizens of their own country. The objective of spying on other countries is to extract information about biomedical and pharmaceutical research related to COVID-19. Sensitive information about research on cures, vaccines, possible treatments, infection data, or internal information on the measures to contain the pandemic appear to be the target of these attacks. Targeted industries hardest hit have been in healthcare, biomedical research, and the public sector.
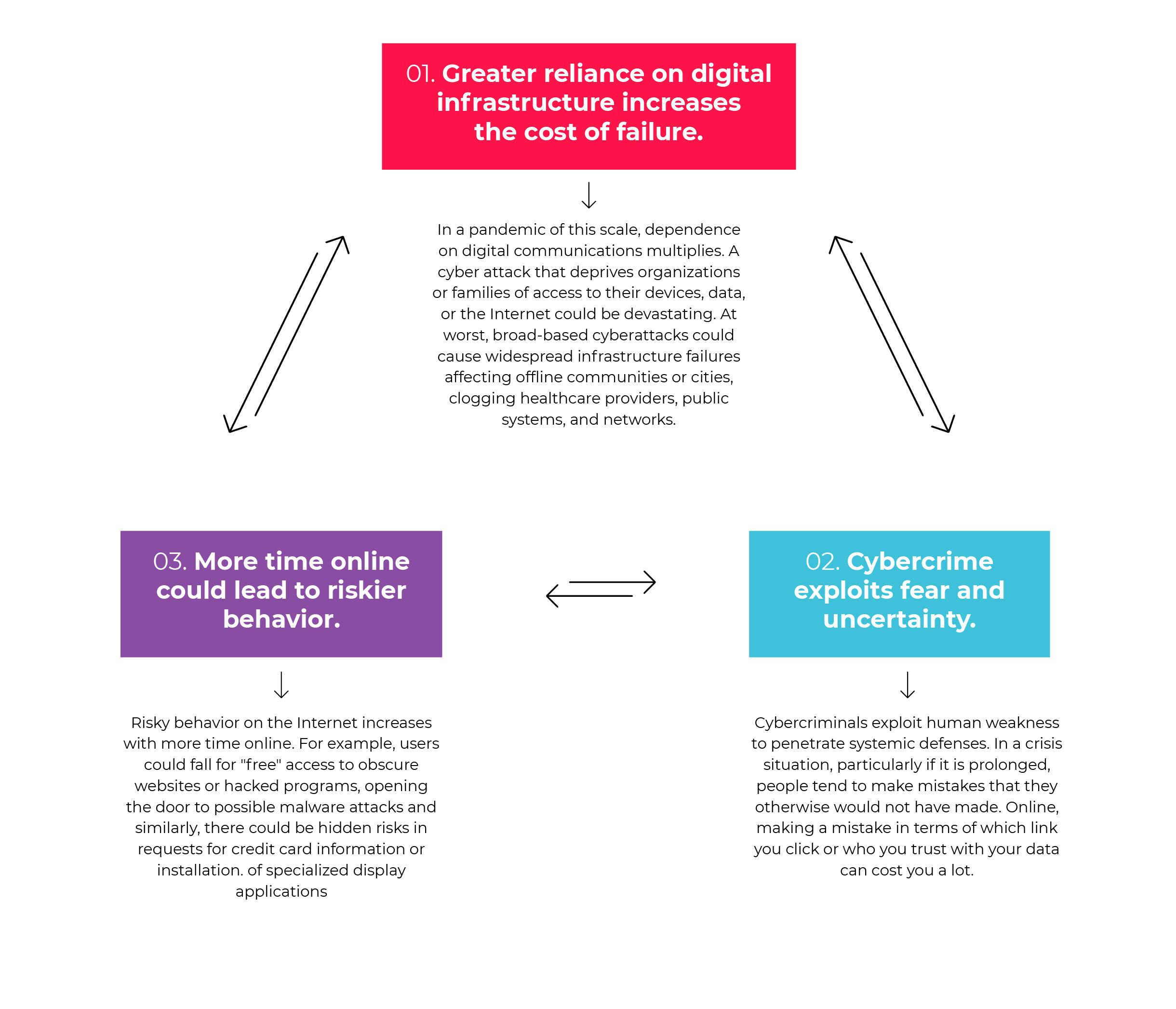
The World Economic Forum proposes the following three reasons why strong cybersecurity measures are more important than ever in today’s world:
So what to do to prevent being victims?
Just as tackling the COVID-19 pandemic requires changing our social habits and routines to prevent infection rates, a change in our behavior online can help maintain high levels of cybersecurity.
Here are three practical actions you can take to stay safe online:
1- Step up your cyber hygiene standards
In addition to washing your hands after each physical contact to prevent the spread of COVID-19, check that you have a long and complex password for your home Wi-Fi and that system firewalls are active. Make sure you don’t reuse passwords on the web and use a reliable VPN to access the internet whenever possible.
2- Be more vigilant in verification
Be much more careful than usual when installing software and providing personal information. Do not click on the links in email. When subscribing to new services, check the URL source and make sure that the programs or applications you install are the original versions from a trusted source. Digital viruses spread much like physical viruses; your potential online mistakes could very well contaminate others in your organization, an address book, or the community at large.
3- Follow the official updates
Just as you pay attention to reliable data sources on the spread and impact of COVID-19, be sure to regularly update your system software and applications to repair any weaknesses. If you feel that the advice you are receiving sounds strange, whether the virus threat is offline or digital, search the internet to see if others have similar concerns and look for a known site that can help verify the information’s legitimacy.
Some of the confirmed attacks during the spread of the pandemic:
| Attack Type | Description of the attack |
| Identity Impersonations | -On February 20, the Public Health Center of the Ministry of Health of Ukraine was impersonated in a phishing campaign of malicious attachments that included information on the latest news about COVID-19 in the country triggering severe incidents in Ukraine. – On March 19, the identity of the Director General of the World Health Organization (WHO) was impersonated in a phishing campaign with attachments that contain alleged instructions about drugs against COVID-19. The email contained an executable file (.exe), the HawkEye keylogger, capable of stealing data from email clients such as Firefox, Thunderbird, Postbox, SeaMonkey, WaterFox, or PaleMoon. |
| Targeted Attacks | • On March 13, the Brno University Hospital in the Czech Republic suffered an attack that caused the shutdown of computer systems, delaying the results of tests on cases of COVID-19. • On March 15, the US Department of Health encountered a failed DDoS attack on its computer systems. According to the US Secretary of Health Alex Azar, there was no intrusion into internal networks and suspects a foreign country could be behind the incident. |
| Cyber Espionage Campaigns | • At the end of February, a campaign of attacks carried out by an APT group linked to China, tracked as “Mustang Panda”, who previously launched attacks against MIAT Airlines, based in Mongolia, and countries including, among others, Germany, Mongolia, Myanmar (Burma), Pakistan, Vietnam. The APT group sent phishing messages with a RAR file that allegedly included information about the Vietnamese prime minister’s COVID-19 outbreak. • In mid-February, experts from the cybersecurity company QiAnXin Technology discovered a campaign targeting people in Ukraine using emails pretending to be from the Public Health Center of the Ministry of Health of Ukraine. Experts believe that the group behind the attack is the Hades APT, a Russian cyberespionage group linked to the APT28 nation-state group. • At the end of March, a Chinese cyber-espionage group called “Vicious Panda” was carrying out a spear-phishing campaign using the pandemic to spread their malware. The emails claim to have information about the COVID-19, with two malicious RTF (Rich Text Format) files attached. If the victim opens these files, a RAT (Remote Access Trojan) launches. These files are capable of taking screenshots, making lists of files, creating directories on the victim’s computer, and downloading files; among other capabilities. So far, only the Mongolian public sector reports being attacked by this campaign. • The Iranian government and its Ministry of Health carried out an internal cyber-espionage campaign, sending SMS to Iranian mobile phone users with links to download an application to assess possible symptoms of COVID-19 in the absence of evidence. The application monitored the actions of the user who downloaded the app. |
| Malware & Ransomware | • “Emails addressed to parents and caregivers” have been detected with a computer virus named “Ursnif” that can steal information such as bank accounts and others directed to health organizations, offering remedies for COVID-19 in exchange for bitcoins. • The use of an unknown malware called RedLine Stealer takes advantage of people’s predisposition to help find a cure for COVID-19 through a computer project distributed for disease research. • The NetWalker computer virus threatens Spanish hospitals. This ransomware locks the victim’s computer systems and asks for a ransom in exchange for the key to free them. |
| Malicious Applications | • COVID-19- Interactive Map: AZORult malware, hid on a map showing COVID-19 statistics uploaded from a legitimate online source. Viewers were asked to download and run a malicious application that compromised the computer and allowed hackers to access stored passwords. } • CovidLock – Mobile App: offers the function of real-time monitoring of those affected by COVID-19. When installed, it requests various permissions such as running in the background, having access to the lock screen, or using Android’s accessibility functionalities to have system administrator permissions and take control of the device. Similar to ransomware, a request for payment is demanded to recover the functionality of the device, threatening to send compromising photos and videos to a contact list in case of non-payment. |

